- Connect Kubernetes services via a secure tunnel with Restate Operator.
- Connect serverless functions (Vercel, Cloudflare Workers, Deno Deploy, etc.) or other public endpoints, by signing requests with your cloud environment’s public key.
- Connect AWS Lambda functions, by granting Restate Cloud permission to assume a role in your AWS account.
- Connect services in private environments, by setting up a tunnel.
Kubernetes services
You can connect your Kubernetes services to Restate Cloud using a secure tunnel provided by the Restate Operator. This allows you to run your services inside a private Kubernetes cluster without exposing them to the public internet. The operator will:- Establish a tunnel to Restate Cloud
- Register your services automatically
- Manage multiple deployment revisions
- Scale down old revisions when no longer needed
Try connecting a greeter service on a local kind Kubernetes cluster to Restate Cloud by following this guide.
Operator deployment
Install the Restate Operator via Helm:Create a Restate Cloud secret
Create an API key viaDevelopers tab of the Restate Cloud UI and give it Full permissions.
The API key starts with key_. Save it in a file named token and create the secret in Kubernetes:
Set up a secure tunnel
Set up a secure tunnel between the Kubernetes cluster and Restate Cloud with theRestateCloudEnvironment CRD:
-
The
environmentIdcan be found in the Restate Cloud UI in the top left corner when you select your environment. This ID starts withenv_. -
The
signingPublicKeycan be found in the Restate Cloud UI underDevelopers. Scroll down to theSecuritysection to find the public key underHTTP endpoints. The public key starts withpublickeyv1_. -
Set the
regionfield to the region your Restate Cloud environment is hosted in. Possible values areusandeu. You can find the region next to your environment ID in the Restate Cloud UI.
RestateCloudEnvironment resource, refer to the Custom Resource Definition (CRD): Pkl (recommended) or YAML.
Create your RestateDeployment
Create aRestateDeployment manifest for your service, as described in the deployment documentation, and specify the cloud environment to register with in the spec:
Serverless Functions and other public endpoints
Restate can invoke your services over the public internet. This is useful if you are deploying your services as serverless functions, e.g. on Vercel, Cloudflare Workers, or Deno Deploy. You can also securely deploy Restate services you operate as directly reachable endpoints.For AWS Lambda, please see the AWS Lambda functions section below.
AWS Lambda functions
Restate Cloud can securely invoke your AWS Lambda functions by assuming an AWS role which you manage, and has appropriate permissions to invoke the relevant functions.Setting up the invoker role
Restate Cloud must be able to assume an AWS role with permission to performlambda:InvokeFunction, within the same AWS account where the Lambda function is deployed. As Restate Cloud is a multi-tenant system, the role must be set up to only allow specifically enumerated Restate Cloud environment(s) you trust to assume it.
Note that the Restate Cloud role is separate from your Lambda function’s execution role.
The execution role is used by your function to perform its tasks, while the invoker role grants Restate Cloud permission to invoke your service handler functions — and nothing else.
You can set up the role directly in IAM or use an infrastructure-as-code tool such as AWS CDK to define it.
IAM trust policy for Restate Cloud
To create a new IAM role, you can copy the trust policy directly from the Restate Cloud UI, by visiting Developers > Security > AWS Lambda. The trust policy allows the Restate Cloud IAM identity to assume the invoker role, only on behalf of the specified environment ID.Using AWS CDK
You can use AWS CDK together with the Restate CDK construct library to deploy Lambda handlers, manage the invoker role, and automatically register Lambda-backed services with a Restate (Cloud) environment. Here is an example CDK stack that deploys a Lambda function and registers it with Restate Cloud:-
The
RESTATE_ENV_IDcan be found in the Restate Cloud UI in the top left corner when you select your environment. This ID starts withenv_. -
For the
RESTATE_API_KEY, create an API key viaDeveloperstab of the Restate Cloud UI and give itFullpermissions.
RestateCloudEnvironment automatically creates an IAM role with an appropriate trust policy for the matching Restate Cloud environment. The ServiceDeployer construct automatically grants this role permission to invoke any AWS Lambda functions registered with the environment. For more details, consult the relevant Restate CDK constructs’ API documentation.
Register your Lambda function
Once you have created the invoker role, you can register your Lambda-backed service(s) with your Restate environment by specifying the role to be assumed:Securing your services:If your Lambda has an appropriate trust policy as described above, you do not
need to secure incoming requests any further. If you choose to however, the
identity verification checks will work on Lambda endpoints as well.
Services in private environments
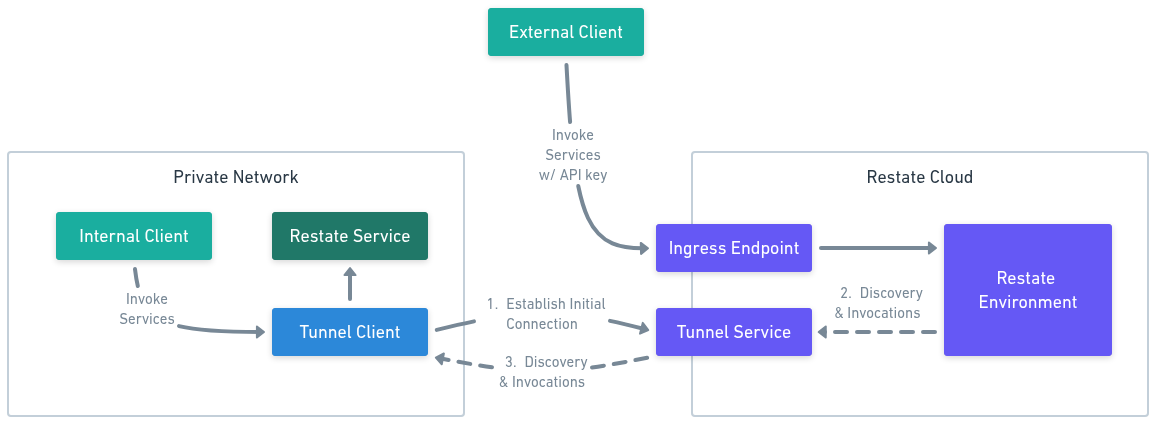
You can connect services that run in a locked-down private environment to Restate Cloud using a secure tunnel. This allows you to expose your services to Restate Cloud without opening up ports to the public internet. The tunnel will also act as an authenticating proxy to Restate Cloud and make it appear as if your Restate Cloud environment is inside your private network. This allows you to use native access control mechanisms, like VPC Security Groups and Kubernetes network policies, to manage access to your Cloud environment. It also lets you control connections from the Cloud environment to the rest of your network by restricting which internal services the tunnel client can connect to.Set up a secure tunnel
The tunnel can be hosted as a cloud VM in your VPC, a sidecar to your service, or a dedicated pod in your container orchestrator. You can deploy multiple copies for redundancy. To run the tunnel:Environment variables
Environment variables
RESTATE_ENVIRONMENT_IDis the environment id (including theenv_prefix).RESTATE_BEARER_TOKENis the API key you created in step 1.RESTATE_TUNNEL_NAMEis a name for the tunnel. Choose a unique DNS-friendly tunnel name, e.g.prod-tunnel.RESTATE_SIGNING_PUBLIC_KEYis the public key you copied from the Cloud UI in step 1.RESTATE_CLOUD_REGIONis the region of your Restate Cloud environment, e.g.euorus.- You can run
latestor pin the current version, e.g.0.4.0 - The health check URL is at
:9090/health
Tunnel ports
Tunnel ports
The tunnel client exposes the following ports
9090tunnel’s own health status8080Restate Ingress (authenticating proxy)9070Restate Admin API (authenticating proxy)
Register your service
If your setup is correct, you can now register your service with the Restate Cloud environment:- Use just the numeric environment id here (without the
env_prefix). - The tunnel name must match the name provided to the tunnel client
- The remote fqdn and port must resolve to the Restate service endpoint (e.g.
localhost:9080) from the perspective of the tunnel client
localhost:9080 and your environment id is env_20d1231jyphzkm8 in region eu, you can register it like this:
How does the tunnel work
- Restate CLI is communicating with your Restate environment at
https://*.eu.restate.cloud:9070using your user ID token and asks the admin API to perform a discovery at the special tunnel URL. - The Restate Cloud end of the tunnel receives the request from your environment and forwards the traffic to the tunnel container.
- The tunnel container is forwarding the traffic to the Restate service endpoint.
Advanced topics
Client-side encryption
You can optionally configure client-side encryption, which makes your data opaque to Restate Cloud. In this case, the SDK encrypts journal entries after serializing them but before sending them to Restate Cloud. What is encrypted? Only the following journal entries are encrypted:- The input and output parameters to the handler
ctx.runsuccess results- RPC calls parameters and return values (for service-to-service invocations)
- State values
- Awakeables and Durable Promise results
JournalValueCodec and provide it to the SDK when creating the endpoint.
Currently, this feature is only available in the TypeScript SDK.
Have a look at a reference implementation that uses Amazon’s KMS to manage encryption keys.
